#include <tlsvalidator.h>
Public Member Functions | |
| CheckResult | activated () |
| If the activation value is in the past. | |
| CheckResult | authorityMatch () |
| Check if the authority match the certificate. | |
| CheckResult | exist () |
| The file has been found. | |
| CheckResult | expectedOwner () |
| The CA and certificate provide conflicting ownership information. | |
| CheckResult | getActivationDate () |
| Get the activation date. | |
| std::shared_ptr< dht::crypto::Certificate > | getCertificate () const |
| CheckResult | getCN () |
| The 'CN' section of a DN (RFC4514) | |
| CheckResult | getExpirationDate () |
| Get the expiration date. | |
| CheckResult | getIssuer () |
| If the certificate is not self signed, return the issuer. | |
| CheckResult | getIssuerCN () |
| If the certificate is not self signed, return the issuer CN. | |
| CheckResult | getIssuerDN () |
| If the certificate is not self signed, return the issuer DN (RFC4514) | |
| CheckResult | getIssuerN () |
| If the certificate is not self signed, return the issuer N. | |
| CheckResult | getIssuerO () |
| If the certificate is not self signed, return the issuer O. | |
| CheckResult | getIssuerUID () |
| If the certificate is not self signed, return the issuer UID. | |
| CheckResult | getMd5Fingerprint () |
| Compute the key fingerprint. | |
| CheckResult | getN () |
| The 'N' section of a DN (RFC4514) | |
| CheckResult | getO () |
| The 'O' section of a DN (RFC4514) | |
| CheckResult | getPublicKeyId () |
| Return an hexadecimal identifier. | |
| CheckResult | getPublicSignature () |
| An hexadecimal representation of the signature. | |
| std::map< std::string, std::string > | getSerializedChecks () |
| Convert all checks results into a string map. | |
| std::map< std::string, std::string > | getSerializedDetails () |
| Get a map with all common certificate details. | |
| CheckResult | getSerialNumber () |
| Return the certificate serial number. | |
| CheckResult | getSha1Fingerprint () |
| Compute the key fingerprint. | |
| CheckResult | getSignatureAlgorithm () |
| Return the algorithm used to sign the Key. | |
| CheckResult | getSubjectKey () |
| The subject public key. | |
| CheckResult | getSubjectKeyAlgorithm () |
| The algorithm used to sign the certificate details (rather than the certificate itself) | |
| CheckResult | getUID () |
| The 'UID' section of a DN (RFC4514) | |
| CheckResult | getVersionNumber () |
| Return the certificate version. | |
| bool | hasCa () const |
| A certificate authority has been provided. | |
| CheckResult | hasPrivateKey () |
| Check if the Validator have access to a private key. | |
| CheckResult | isCA () |
| If the certificate is not self signed, return the issuer. | |
| bool | isValid (bool verbose=false) |
| Check if all boolean check passed return true if there was no FAILED checks. | |
| CheckResult | keyMatch () |
| The provided key can be used along with the certificate. | |
| CheckResult | knownAuthority () |
| When an account require an authority known by the system (like /usr/share/ssl/certs) then the whole chain of trust need be to checked. | |
| CheckResult | notExpired () |
| Check if the certificate is not expired. | |
| CheckResult | notRevoked () |
| Check if the certificate has been revoked. | |
| CheckResult | notSelfSigned () |
| The certificate is not self signed. | |
| CheckResult | outgoingServer () |
| The expected outgoing server domain. | |
| CheckResult | privateKeyDirectoryPermissions () |
| CheckResult | privateKeySelinuxAttributes () |
| SELinux provide additional key protection mechanism. | |
| CheckResult | privateKeyStorageLocation () |
| Certificate should be located in specific path on some operating systems. | |
| CheckResult | privateKeyStoragePermissions () |
| CheckResult | publicKeyDirectoryPermissions () |
| CheckResult | publicKeySelinuxAttributes () |
| SELinux provide additional key protection mechanism. | |
| CheckResult | publicKeyStorageLocation () |
| Certificate should be located in specific path on some operating systems. | |
| CheckResult | publicKeyStoragePermissions () |
| CheckResult | requirePrivateKeyPassword () |
| If the key need decryption. | |
| void | setCaTlsValidator (const TlsValidator &validator) |
| CheckResult | strongSigning () |
| If the algorithm used to sign the certificate is considered weak by modern standard. | |
| TlsValidator (const dhtnet::tls::CertificateStore &certStore, const std::shared_ptr< dht::crypto::Certificate > &) | |
| TlsValidator (const dhtnet::tls::CertificateStore &certStore, const std::string &certificate, const std::string &privatekey="", const std::string &privatekeyPasswd="", const std::string &caList="") | |
| Create a TlsValidator for a given certificate. | |
| TlsValidator (const dhtnet::tls::CertificateStore &certStore, const std::vector< std::vector< uint8_t > > &certificate_chain_raw) | |
| TlsValidator (const dhtnet::tls::CertificateStore &certStore, const std::vector< uint8_t > &certificate_raw) | |
| CheckResult | valid () |
| The certificate is invalid compared to the authority. | |
| CheckResult | validAuthority () |
| The provided authority is invalid. | |
| ~TlsValidator () | |
Detailed Description
Definition at line 68 of file tlsvalidator.h.
Member Typedef Documentation
◆ CheckResult
| using jami::tls::TlsValidator::CheckResult = std::pair<CheckValues, std::string> |
Definition at line 176 of file tlsvalidator.h.
Member Enumeration Documentation
◆ CertificateCheck
All validation fields.
Definition at line 75 of file tlsvalidator.h.
◆ CertificateDetails
Informative fields about a certificate.
Definition at line 109 of file tlsvalidator.h.
◆ CheckValues
Definition at line 159 of file tlsvalidator.h.
◆ CheckValuesType
Categories of possible values for each CertificateCheck.
| Enumerator | |
|---|---|
| BOOLEAN | |
| ISO_DATE | |
| CUSTOM | |
| NUMBER | |
| COUNT__ | |
Definition at line 141 of file tlsvalidator.h.
Constructor & Destructor Documentation
◆ TlsValidator() [1/4]
| jami::tls::TlsValidator::TlsValidator | ( | const dhtnet::tls::CertificateStore & | certStore, |
| const std::string & | certificate, | ||
| const std::string & | privatekey = "", |
||
| const std::string & | privatekeyPasswd = "", |
||
| const std::string & | caList = "" |
||
| ) |
Create a TlsValidator for a given certificate.
- Parameters
-
certificate The certificate path privatekey An optional private key file path privatekeyPasswd An optional private key password caList An optional CA list to use for certificate validation
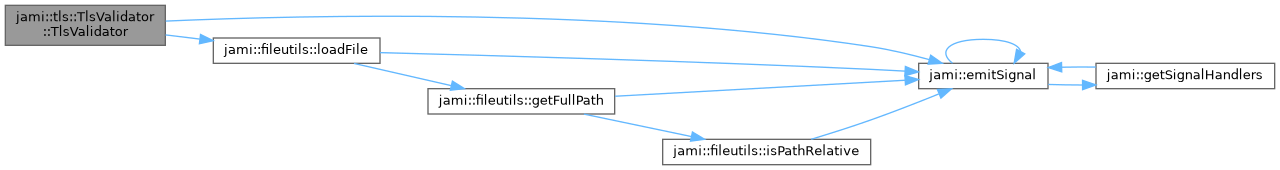
Definition at line 234 of file tlsvalidator.cpp.
References jami::emitSignal(), JAMI_WARN, and jami::fileutils::loadFile().
◆ TlsValidator() [2/4]
| jami::tls::TlsValidator::TlsValidator | ( | const dhtnet::tls::CertificateStore & | certStore, |
| const std::vector< std::vector< uint8_t > > & | certificate_chain_raw | ||
| ) |
Definition at line 230 of file tlsvalidator.cpp.
◆ TlsValidator() [3/4]
| jami::tls::TlsValidator::TlsValidator | ( | const dhtnet::tls::CertificateStore & | certStore, |
| const std::vector< uint8_t > & | certificate_raw | ||
| ) |
Definition at line 278 of file tlsvalidator.cpp.
References jami::emitSignal().

◆ TlsValidator() [4/4]
| jami::tls::TlsValidator::TlsValidator | ( | const dhtnet::tls::CertificateStore & | certStore, |
| const std::shared_ptr< dht::crypto::Certificate > & | crt | ||
| ) |
Definition at line 290 of file tlsvalidator.cpp.
References jami::emitSignal().

◆ ~TlsValidator()
| jami::tls::TlsValidator::~TlsValidator | ( | ) |
Definition at line 304 of file tlsvalidator.cpp.
Member Function Documentation
◆ activated()
| TlsValidator::CheckResult jami::tls::TlsValidator::activated | ( | ) |
If the activation value is in the past.
@fixme Handle both "with ca" and "without ca" case
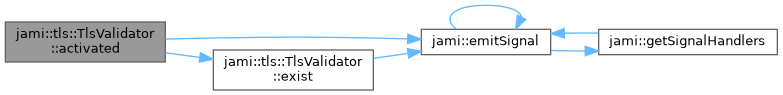
Definition at line 798 of file tlsvalidator.cpp.
References jami::emitSignal(), exist(), FAILED, PASSED, and UNSUPPORTED.
◆ authorityMatch()
| TlsValidator::CheckResult jami::tls::TlsValidator::authorityMatch | ( | ) |
Check if the authority match the certificate.
Definition at line 1062 of file tlsvalidator.cpp.
References jami::emitSignal(), FAILED, and PASSED.

◆ exist()
| TlsValidator::CheckResult jami::tls::TlsValidator::exist | ( | ) |
The file has been found.
Definition at line 1025 of file tlsvalidator.cpp.
References jami::emitSignal(), FAILED, and PASSED.
Referenced by activated(), getSerializedChecks(), keyMatch(), notExpired(), and strongSigning().

◆ expectedOwner()
| TlsValidator::CheckResult jami::tls::TlsValidator::expectedOwner | ( | ) |
The CA and certificate provide conflicting ownership information.
Definition at line 1013 of file tlsvalidator.cpp.
References jami::emitSignal(), FAILED, and PASSED.

◆ getActivationDate()
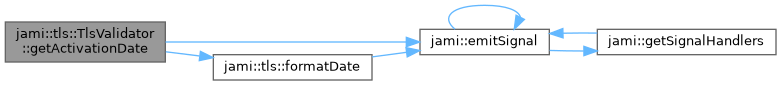
| TlsValidator::CheckResult jami::tls::TlsValidator::getActivationDate | ( | ) |
Get the activation date.
- Todo:
- Move to "certificateDetails()" method once completed
Definition at line 1444 of file tlsvalidator.cpp.
References jami::emitSignal(), jami::tls::formatDate(), and UNSUPPORTED.
◆ getCertificate()
|
inline |
Definition at line 258 of file tlsvalidator.h.
Referenced by libjami::getCertificateDetails(), and libjami::validateCertificate().
◆ getCN()
| TlsValidator::CheckResult jami::tls::TlsValidator::getCN | ( | ) |
The 'CN' section of a DN (RFC4514)
Definition at line 1217 of file tlsvalidator.cpp.
References jami::tls::checkError(), and jami::emitSignal().

◆ getExpirationDate()
| TlsValidator::CheckResult jami::tls::TlsValidator::getExpirationDate | ( | ) |
Get the expiration date.
- Todo:
- Move to "certificateDetails()" method once completed
Definition at line 1428 of file tlsvalidator.cpp.
References jami::emitSignal(), jami::tls::formatDate(), and UNSUPPORTED.
◆ getIssuer()
| TlsValidator::CheckResult jami::tls::TlsValidator::getIssuer | ( | ) |
If the certificate is not self signed, return the issuer.
Definition at line 1163 of file tlsvalidator.cpp.
References CUSTOM, jami::emitSignal(), and UNSUPPORTED.

◆ getIssuerCN()
| TlsValidator::CheckResult jami::tls::TlsValidator::getIssuerCN | ( | ) |
If the certificate is not self signed, return the issuer CN.
Definition at line 1362 of file tlsvalidator.cpp.
References jami::tls::checkError(), and jami::emitSignal().

◆ getIssuerDN()
| TlsValidator::CheckResult jami::tls::TlsValidator::getIssuerDN | ( | ) |
If the certificate is not self signed, return the issuer DN (RFC4514)
Definition at line 1351 of file tlsvalidator.cpp.
References jami::tls::checkError(), and jami::emitSignal().

◆ getIssuerN()
| TlsValidator::CheckResult jami::tls::TlsValidator::getIssuerN | ( | ) |
If the certificate is not self signed, return the issuer N.
Definition at line 1394 of file tlsvalidator.cpp.
References jami::tls::checkError(), and jami::emitSignal().

◆ getIssuerO()
| TlsValidator::CheckResult jami::tls::TlsValidator::getIssuerO | ( | ) |
If the certificate is not self signed, return the issuer O.
Definition at line 1410 of file tlsvalidator.cpp.
References jami::tls::checkError(), and jami::emitSignal().

◆ getIssuerUID()
| TlsValidator::CheckResult jami::tls::TlsValidator::getIssuerUID | ( | ) |
If the certificate is not self signed, return the issuer UID.
Definition at line 1378 of file tlsvalidator.cpp.
References jami::tls::checkError(), and jami::emitSignal().

◆ getMd5Fingerprint()
| TlsValidator::CheckResult jami::tls::TlsValidator::getMd5Fingerprint | ( | ) |
Compute the key fingerprint.
This need to be used along with getSha1Fingerprint() to avoid collisions
Definition at line 1304 of file tlsvalidator.cpp.
References jami::tls::checkBinaryError(), and jami::emitSignal().

◆ getN()
| TlsValidator::CheckResult jami::tls::TlsValidator::getN | ( | ) |
The 'N' section of a DN (RFC4514)
Definition at line 1250 of file tlsvalidator.cpp.
References jami::tls::checkError(), and jami::emitSignal().

◆ getO()
| TlsValidator::CheckResult jami::tls::TlsValidator::getO | ( | ) |
The 'O' section of a DN (RFC4514)
Definition at line 1267 of file tlsvalidator.cpp.
References jami::tls::checkError(), and jami::emitSignal().

◆ getPublicKeyId()
| TlsValidator::CheckResult jami::tls::TlsValidator::getPublicKeyId | ( | ) |
Return an hexadecimal identifier.
Definition at line 1334 of file tlsvalidator.cpp.
References jami::tls::checkBinaryError(), and jami::emitSignal().

◆ getPublicSignature()
| TlsValidator::CheckResult jami::tls::TlsValidator::getPublicSignature | ( | ) |
An hexadecimal representation of the signature.
Definition at line 1123 of file tlsvalidator.cpp.
References jami::tls::checkBinaryError(), and jami::emitSignal().

◆ getSerializedChecks()
| std::map< std::string, std::string > jami::tls::TlsValidator::getSerializedChecks | ( | ) |
Convert all checks results into a string map.
Definition at line 361 of file tlsvalidator.cpp.
References jami::emitSignal(), EXIST, and exist().
Referenced by libjami::validateCertificatePath().
◆ getSerializedDetails()
| std::map< std::string, std::string > jami::tls::TlsValidator::getSerializedDetails | ( | ) |
Get a map with all common certificate details.
Definition at line 381 of file tlsvalidator.cpp.
References CUSTOM, jami::emitSignal(), FAILED, ISO_DATE, NUMBER, PASSED, and UNSUPPORTED.
Referenced by libjami::getCertificateDetailsPath().

◆ getSerialNumber()
| TlsValidator::CheckResult jami::tls::TlsValidator::getSerialNumber | ( | ) |
Return the certificate serial number.
Definition at line 1150 of file tlsvalidator.cpp.
References jami::tls::checkBinaryError(), and jami::emitSignal().

◆ getSha1Fingerprint()
| TlsValidator::CheckResult jami::tls::TlsValidator::getSha1Fingerprint | ( | ) |
Compute the key fingerprint.
This need to be used along with getMd5Fingerprint() to avoid collisions
Definition at line 1320 of file tlsvalidator.cpp.
References jami::tls::checkBinaryError(), and jami::emitSignal().

◆ getSignatureAlgorithm()
| TlsValidator::CheckResult jami::tls::TlsValidator::getSignatureAlgorithm | ( | ) |
Return the algorithm used to sign the Key.
For example: RSA
Definition at line 1286 of file tlsvalidator.cpp.
References CUSTOM, jami::emitSignal(), and UNSUPPORTED.

◆ getSubjectKey()
| TlsValidator::CheckResult jami::tls::TlsValidator::getSubjectKey | ( | ) |
The subject public key.
Definition at line 1202 of file tlsvalidator.cpp.
References CUSTOM, jami::emitSignal(), and UNSUPPORTED.

◆ getSubjectKeyAlgorithm()
| TlsValidator::CheckResult jami::tls::TlsValidator::getSubjectKeyAlgorithm | ( | ) |
The algorithm used to sign the certificate details (rather than the certificate itself)
Definition at line 1178 of file tlsvalidator.cpp.
References CUSTOM, jami::emitSignal(), and UNSUPPORTED.

◆ getUID()
| TlsValidator::CheckResult jami::tls::TlsValidator::getUID | ( | ) |
The 'UID' section of a DN (RFC4514)
Definition at line 1234 of file tlsvalidator.cpp.
References jami::tls::checkError(), and jami::emitSignal().

◆ getVersionNumber()
| TlsValidator::CheckResult jami::tls::TlsValidator::getVersionNumber | ( | ) |
Return the certificate version.
Definition at line 1134 of file tlsvalidator.cpp.
References jami::emitSignal(), NUMBER, UNSUPPORTED, and jami::swarm_protocol::version.

◆ hasCa()
| bool jami::tls::TlsValidator::hasCa | ( | ) | const |
A certificate authority has been provided.
Definition at line 1107 of file tlsvalidator.cpp.
References jami::emitSignal().

◆ hasPrivateKey()
| TlsValidator::CheckResult jami::tls::TlsValidator::hasPrivateKey | ( | ) |
Check if the Validator have access to a private key.
Definition at line 757 of file tlsvalidator.cpp.
References jami::emitSignal(), FAILED, JAMI_DBG, and PASSED.

◆ isCA()
| TlsValidator::CheckResult jami::tls::TlsValidator::isCA | ( | ) |
If the certificate is not self signed, return the issuer.
Definition at line 1471 of file tlsvalidator.cpp.
References CUSTOM, jami::FALSE_STR, and jami::TRUE_STR.
◆ isValid()
Check if all boolean check passed return true if there was no FAILED checks.
Checks functions are not "const", so this function isn't
Definition at line 343 of file tlsvalidator.cpp.
References BOOLEAN, jami::emitSignal(), FAILED, and JAMI_WARNING.

◆ keyMatch()
| TlsValidator::CheckResult jami::tls::TlsValidator::keyMatch | ( | ) |
The provided key can be used along with the certificate.
Definition at line 842 of file tlsvalidator.cpp.
References jami::emitSignal(), exist(), FAILED, PASSED, and UNSUPPORTED.
◆ knownAuthority()
| TlsValidator::CheckResult jami::tls::TlsValidator::knownAuthority | ( | ) |
When an account require an authority known by the system (like /usr/share/ssl/certs) then the whole chain of trust need be to checked.
@fixme port crypto_cert_load_trusted @fixme add account settings
- Todo:
- implement the check
Definition at line 1079 of file tlsvalidator.cpp.
References jami::emitSignal(), FAILED, and PASSED.

◆ notExpired()
| TlsValidator::CheckResult jami::tls::TlsValidator::notExpired | ( | ) |
Check if the certificate is not expired.
The double negative is used because all boolean checks need to have a consistent return value semantic
@fixme Handle both "with ca" and "without ca" case
Definition at line 781 of file tlsvalidator.cpp.
References jami::emitSignal(), exist(), FAILED, PASSED, and UNSUPPORTED.
◆ notRevoked()
| TlsValidator::CheckResult jami::tls::TlsValidator::notRevoked | ( | ) |
Check if the certificate has been revoked.
Definition at line 1093 of file tlsvalidator.cpp.
References jami::emitSignal(), FAILED, and PASSED.

◆ notSelfSigned()
| TlsValidator::CheckResult jami::tls::TlsValidator::notSelfSigned | ( | ) |
The certificate is not self signed.
Definition at line 833 of file tlsvalidator.cpp.
References UNSUPPORTED.
◆ outgoingServer()
| TlsValidator::CheckResult jami::tls::TlsValidator::outgoingServer | ( | ) |
The expected outgoing server domain.
- Todo:
Move to "certificateDetails()" method once completed
extract information for the certificate
Definition at line 1461 of file tlsvalidator.cpp.
References CUSTOM.
◆ privateKeyDirectoryPermissions()
| TlsValidator::CheckResult jami::tls::TlsValidator::privateKeyDirectoryPermissions | ( | ) |
Definition at line 892 of file tlsvalidator.cpp.
References jami::emitSignal(), FAILED, PASSED, S_IRGRP, S_IROTH, S_IRUSR, S_ISDIR, S_IWGRP, S_IWOTH, S_IXGRP, S_IXOTH, S_IXUSR, and UNSUPPORTED.

◆ privateKeySelinuxAttributes()
| TlsValidator::CheckResult jami::tls::TlsValidator::privateKeySelinuxAttributes | ( | ) |
SELinux provide additional key protection mechanism.
Definition at line 982 of file tlsvalidator.cpp.
References UNSUPPORTED.
◆ privateKeyStorageLocation()
| TlsValidator::CheckResult jami::tls::TlsValidator::privateKeyStorageLocation | ( | ) |
Certificate should be located in specific path on some operating systems.
Definition at line 962 of file tlsvalidator.cpp.
References UNSUPPORTED.
◆ privateKeyStoragePermissions()
| TlsValidator::CheckResult jami::tls::TlsValidator::privateKeyStoragePermissions | ( | ) |
Definition at line 854 of file tlsvalidator.cpp.
References jami::emitSignal(), FAILED, PASSED, S_IFREG, S_IRGRP, S_IROTH, S_IRUSR, S_IWGRP, S_IWOTH, S_IXGRP, S_IXOTH, S_IXUSR, and UNSUPPORTED.

◆ publicKeyDirectoryPermissions()
| TlsValidator::CheckResult jami::tls::TlsValidator::publicKeyDirectoryPermissions | ( | ) |
Definition at line 927 of file tlsvalidator.cpp.
References jami::emitSignal(), FAILED, PASSED, S_IRGRP, S_IROTH, S_IRUSR, S_ISDIR, S_IWGRP, S_IWOTH, S_IXGRP, S_IXOTH, S_IXUSR, and UNSUPPORTED.

◆ publicKeySelinuxAttributes()
| TlsValidator::CheckResult jami::tls::TlsValidator::publicKeySelinuxAttributes | ( | ) |
SELinux provide additional key protection mechanism.
Definition at line 992 of file tlsvalidator.cpp.
References UNSUPPORTED.
◆ publicKeyStorageLocation()
| TlsValidator::CheckResult jami::tls::TlsValidator::publicKeyStorageLocation | ( | ) |
Certificate should be located in specific path on some operating systems.
Definition at line 972 of file tlsvalidator.cpp.
References UNSUPPORTED.
◆ publicKeyStoragePermissions()
| TlsValidator::CheckResult jami::tls::TlsValidator::publicKeyStoragePermissions | ( | ) |
Definition at line 873 of file tlsvalidator.cpp.
References jami::emitSignal(), FAILED, PASSED, S_IFREG, S_IRUSR, S_IWGRP, S_IWOTH, S_IXGRP, S_IXOTH, S_IXUSR, and UNSUPPORTED.

◆ requirePrivateKeyPassword()
| TlsValidator::CheckResult jami::tls::TlsValidator::requirePrivateKeyPassword | ( | ) |
If the key need decryption.
Double factor authentication is recommended
Definition at line 1004 of file tlsvalidator.cpp.
◆ setCaTlsValidator()
| void jami::tls::TlsValidator::setCaTlsValidator | ( | const TlsValidator & | validator | ) |
◆ strongSigning()
| TlsValidator::CheckResult jami::tls::TlsValidator::strongSigning | ( | ) |
If the algorithm used to sign the certificate is considered weak by modern standard.
Definition at line 815 of file tlsvalidator.cpp.
References jami::emitSignal(), exist(), FAILED, PASSED, and UNSUPPORTED.
◆ valid()
| TlsValidator::CheckResult jami::tls::TlsValidator::valid | ( | ) |
The certificate is invalid compared to the authority.
- Todo:
- Handle case when there is facultative authority, such as DHT
Definition at line 1039 of file tlsvalidator.cpp.
◆ validAuthority()
| TlsValidator::CheckResult jami::tls::TlsValidator::validAuthority | ( | ) |
The provided authority is invalid.
Definition at line 1049 of file tlsvalidator.cpp.
References jami::emitSignal(), FAILED, and PASSED.

The documentation for this class was generated from the following files: